The rise of DevSecOps and its challenges.

The rise of DevSecOps and its challenges.

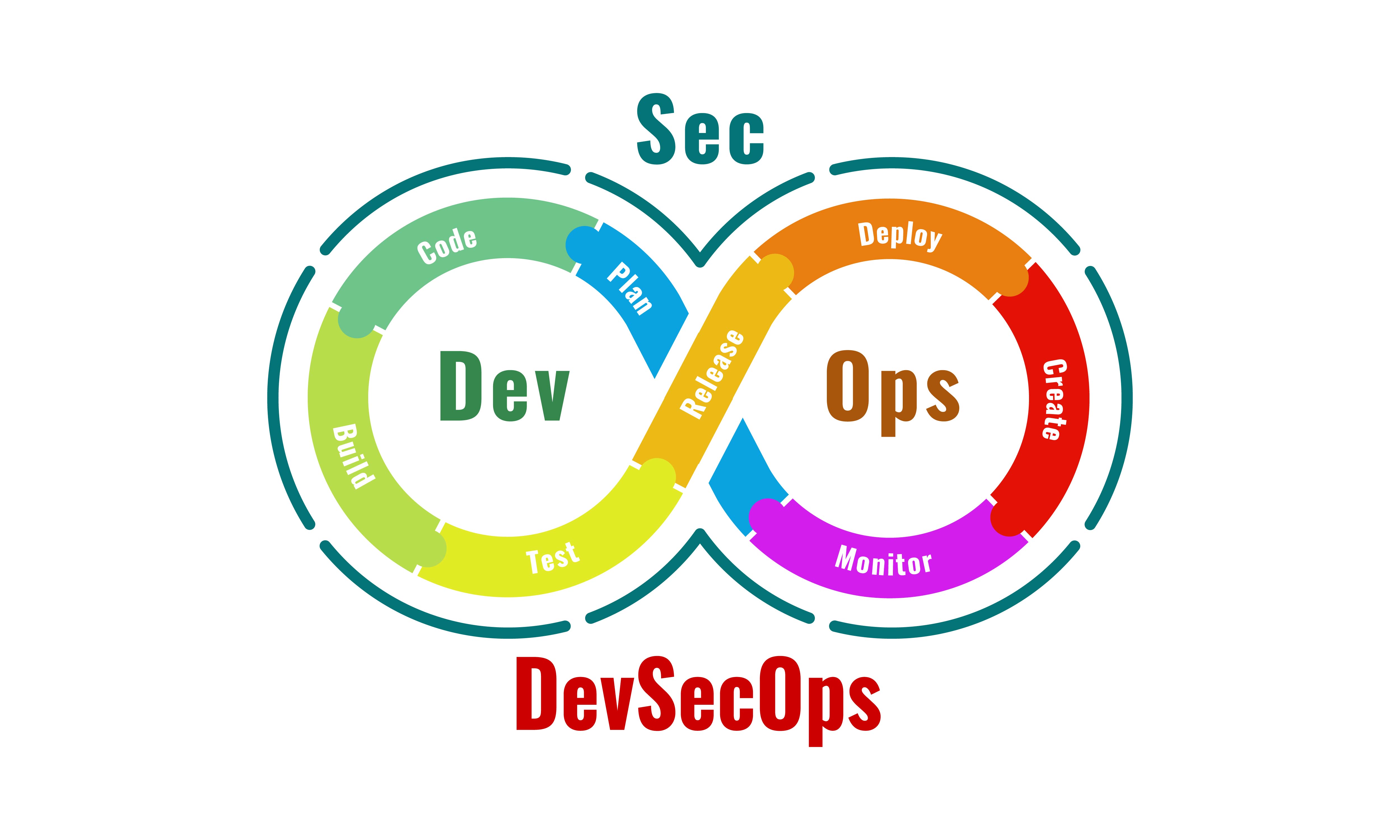
The only constant part of the IT sector is the “Change”. To accommodate the ever-changing demands of businesses, IT sector has adopted agility in the processes but the challenge doesn’t end here. With the realization that Security, one of the most important pillars of the system processes, is being offered the role at the end of system development, the quest started and the outcome is DevSecOps. Here we are to discuss a few key technicalities while instigating DevSecOps in the firm.
What is DevSecOps?DevSecOps is an architecture that embeds the Security check as an integral part of development and integration. It makes sure that a fair equilibrium is maintained between development, Integration, and security. This makes sure that the system is security compliant at every stage of the development life cycle. It enables timely delivery of software in a secure way.
How is my company getting benefitted?It enhances the efficacy of the software development process, makes it cost-effective, avoids rebuilds, and ensures reliable software by integrating security at every development stage.
Is it for my company?Yes, all the small and big IT firms striving for the delivery of secured software can get benefitted from it.
For what all domains it is suitable?It is applicable for application development for all the domains like Health Care, Banking, Telecom, etc.
Healthcare:Since the covid outbreak investors have been pouring millions in the healthcare sector which gave rise to startups with innovate solutions and services. This demands a lot of automation and lower turnaround time for services to reach the end user. DevOps can help healthcare companies invest more time on strategy is it takes care of operations where teams can save lot of time. The healthcare supply chain can be transformed in a huge way by the use of predictive analytics, RFID tracking, patient diagnosis, IoT and inventory management.
Tools such as sumo logic find huge implementation capabilities especially for predictive analytics. IT also uses predictive analytics to provide cloud security. Predictive analytics use huge volumes of data for its analytics which can range from suppliers, healthcare companies, pharmacies, blood banks, to hospitality services, 3rd party vendors and software providers. Various use cases can be solved using Predictive analytics such as
Banking sectors more than any other industry need advanced tools to qualify ideal customers and partners along with doing key activities to develop a sustainable business model. With millions of transections being done every single day, the changes of identifying error gets less. DevSecOps can help to identify cyber security threats such as-
Security tools with features such as low cost maintenance, ease of implementation, flexibility, low code/ no code implementation are available using which application code is made secure with hampering the daily operations/transactions which are taking place. These tools can help to save and share analytics traffic, monitor keys and certificates to identify weakness, allow to make changes in production like scenario without affecting it.
Telecom:Telecom companies are now looking to provide tailored solutions to retain customers by developing service model apart from providing just basic connectivity services. With the introduction of 5G, data centers can transfer data at huge speeds opening up opportunities for developing new capabilities to the end user. With the inclusion of IoT in telecom, real time data collection and analysis have become important to service providers as smartphones can collect user data 24/7. Some of the capabilities with DevOps service providers can develop the ability to analyze busy hours to plan capital investment in network infrastructure, Analyze user behavior during different times of the day to develop tailored plan to attract new user base.
In DevSecOps chances of data braches becomes considerably low because of zero trust control policy. DevSecOps provides in-built capabilities with various tools to implement 5G services due to which service providers do not have to worry about security aspect of data.
What are the Challenges?
Knowledge of security posture at every level: In order to embed the security at every stage of development, the whole team structure including developers, operations, and compliance team has to be aware of the security norms of the firm.
Compliance to Auditability: To ensure compliance with security controls, the auditability of technical, procedural, and management security controls becomes the prerequisite. The processes need to be well-documented and cohere to by all teams.
Resistance to transition: So far security had been the pinnacle performer playing a role at the time of delivery. With the implementation of DevSecOps, security becomes the responsibility of every accountable employee.
Training process: Team needs to be trained for the security process and related compliance.
Mindset: Considering the above-mentioned challenges, an organization has to be consistent and patient to reap the long-term benefits. Once the processes are set and employees are trained, investment in DevSecOps will start bearing fruits. As per Gartner’s report, financial losses due to security issues can be pulled down by 90% by adhering to the Cyber security Mesh Architecture. The essence of the discussion is, DevSecOps needs long-term investment, patience, and consistency at all the development stages to reap the payback. Training and awareness can play a pivotal role in availing the maximum benefit out of it. It will help bring down the financial losses due to security events.